Fraudulent Domains Hiding in Plain Sight with New gTLDs!

For several decades now, people have been familiar with Top-level Domains (TLDs) like .com, .net, .org, etc. In 2014, new TLDs were introduced, and vanity URLs can now be customized further with them. Businesses are able to use their niche or area of expertise as their TLD. For example, as a web app development company, you can create ‘yourcompany[.]tech’ as your domain name. While new gTLDs have several advantages and of course also look great, they come with some strings attached that organizations should be aware of. One problem is trust, while another, which also facilitates the first, is cybersecurity.
Even though the number of domains registered with new gTLD has doubled in 1 year, it may seem to make one believe that people have gladly accepted and adopted these new top-level domains. However, the picture may be different with a deeper analysis. A lot of these registrations are investments of cybercriminals to create false websites to defraud people. The 2016 Global Phishing Survey documented that more than a quarter-million individual phishing sites mimicked the web pages of approximately 700 genuine banks, other e-commerce platforms, finance, and social media companies. The source further notes that about 86% of the phishing sites on the new gTLDs were registered as such, without hacking others. This indicates the propensity of malicious activities that new gTLDs can sponsor.
When the Internet Corporation for Assigned Names and Numbers (ICANN) reported the commencement of new generic TLDs (gTLDs), a rise of 1,200 new TLD domains was announced to become a part of the top-level domains, strengthening hackers to embark on phishing campaigns. Spamhaus had reported a particular domain, .loan, to be the most abused TLD of all time. Although in the seventh position at the moment, with 445 out of 598 domains - 75% - reported as malicious and with a badness index of 4.54.
According to a survey carried out by Varn, most people trusted “.com” and “.co.uk” more than the new gTLDs. Another survey reported by Survey Monkey indicates that 67% of marketers would less likely trust a quote from a website if a customized extension is used.
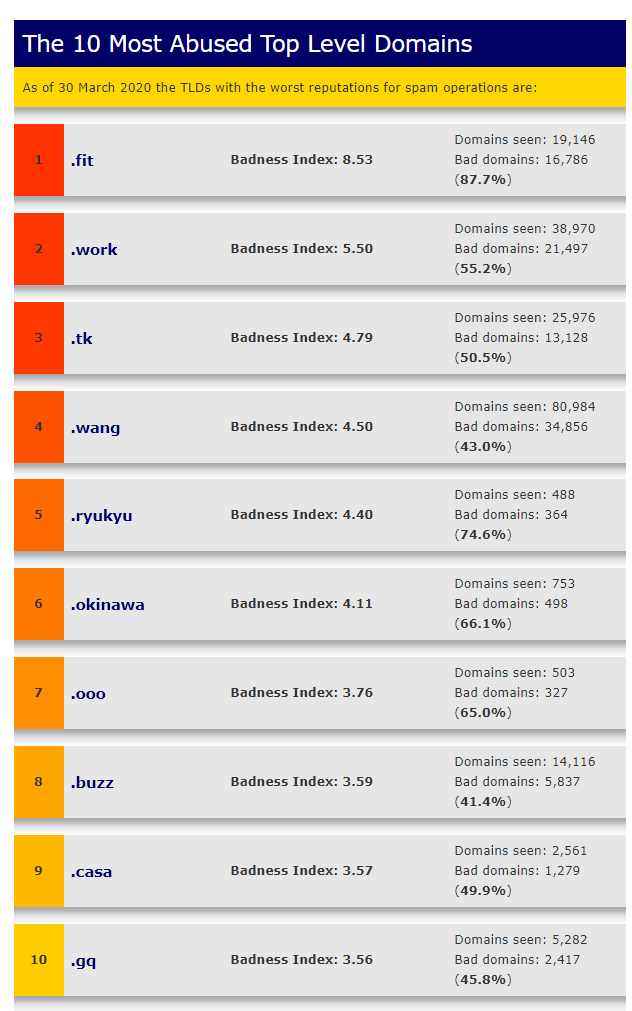
According to Spamhaus, as of February 3, 2020, the most abused top-level domains and their badness index include the following, where new gTLDs take a greater portion on the list than any other individual category.
Security Threats Of New gTLDs
New gTLDs are mostly used for 3 types of abuse by cybercriminals.
1) Phishing
.loan, .club, .xyz, .website are most commonly used for phishing attacks in an attempt to mislead customers and acquire their private information. One of the most employed phishing strategies is domain name spoofing, for which new gTLDs have become a major enhancer. According to Dark Reading, the reasons for continuous phishing growth is because people are likely to click on a link without noticing the ".pop" or ".xyz" when they see a trusted and familiar name in the prefix of the URL.
2) Malware
Bad actors can easily spoof or create typosquatting domains based on known brands and host their exploit kits in such domains. This tricks visitors into installing malware or malicious software on their systems without their knowledge or permission. Once the attacker has access to a user’s system, they can carry out various malicious operations like click fraud, spyware, ransomware, etc.
3) Spam
Approximately 60% of the current spam emails are directed from new gTLDs. With much lower prices for purchasing new gTLD domains, unlike costly legacy TLD domains, these are becoming a preferred choice for such activities. Spammers can now simply buy domains in bulk at a lower cost and send spam emails from multiple domains. Even if the email filters block some domains, others may still manage to escape them.
A Common Case
Long after the launch of new gTLDs, the SANS Institute's Internet Storm Center identified a phishing attack directed at Bank of America’s customers. Attackers used .support new gTLD and set up the phishing page on url-bofa[.]support/BankOfAmerica[.]com. To further mislead victims with the proof of credibility, the attackers got valid SSL certificates via passing a certificate authority's domain control and validation routine. By registering the phishing web page and securing it, cybercriminals made it look more credible.
Conclusively, while some people feel the newly added Top-level Domains can help to publicize what they do, the security threats it poses are much too serious. So, one is left wondering whether it is worth it, despite various sources showing that new gTLDs only possess limited business value. The best protection will be to strengthen every defense point possible on a personal or an organizational network system. If possible, domain names in the related category of the new gTLDs should be purchased and sealed off, to help protect the integrity of a business brand. However, with over 1200 new gTLDs that is not really a viable option.
Whoisology can help domain owners proactively defend their brand reputation. By just typing your domain keyword, you will get a list of all the domain names that are registered. A quick glance can help you find out if there are other domain names registered using those keywords. You not only get a list of these domains, but by simply clicking on the domain name/s, you can also get the domain registration details and know various contact details, when it was registered, server details and other domain connections.
With the growing threat landscape, both brand owners and security professionals alike can use Whoisology to uncover new gTLDs domains that are spoofing brands and could be a potential security threat.